What you’ll learn:
Active Directory (AD) is a directory service introduced by Microsoft as a centralized network resource management system. This network is comprised of entities that represent real users or network resources, and the entities are called Active Directory objects. AD objects can be of several types based on what they represent and their function. In this article, we shall understand what AD objects are, learn about the different types of objects in AD, and see how the objects get their properties.
What is an object in Active Directory?
Active Directory (AD) objects are the building blocks of an Active Directory network. AD objects are entities that represent a resource such as users, computers, or printers that are a part of the AD network. Each object is defined by a set of information about them. These pieces of information are called object attributes. For example, a user’s object’s attributes would have their full name, telephone number, address, and more. These attributes are used to identify or search for objects in the AD network using LDAP queries. Each object type has a pre-defined set of attributes associated with it. These attributes are defined by what is called object classes. You can learn more about object attributes here.
What are object classes?
Every Active Directory network would have what is called a schema. A schema is essentially a database of what attributes each type of object should have in an AD forest. It is a blueprint that gives a skeletal structure for the objects, based on which the objects would be created. Object classes are a part of the schema. Think of it as a template for the objects. Object classes define the attributes that each object should have. There are three types of object classes framed in a hierarchical order: abstract, structural, and auxiliary.
- Abstract class: An abstract class is a top-level class that contains other abstract or structural classes. It defines only the basic attributes of an object.
- Structural class: A structural class is the main component that defines an object and what attributes it should have. A structural class always comes under an abstract class or another structural class.
- Auxiliary class: Auxiliary class contains additional attributes that the other classes can inherit from. These attributes are usually ones that the other classes don’t want to define but can inherit whenever necessary. Auxiliary classes can be subclasses of an abstract class or other auxiliary classes.
You can learn more about object classes and how their hierarchy works here.
How can objects be identified in the Active Directory?
When objects are created in Active Directory, each of them is assigned a 128-bit unique value to them. This value is called a global unique identifier (GUID). Objects in the network can be identified using their GUID. Among all the objects, there is a special category of objects called security principles. These objects are those that can be authenticated by an operating system. Users, computers, and groups are security principles. These security principals, apart from having a GUID, are also assigned another unique identifier called a security identifier (SID). This unique identifier is not assigned to any other object other than users, groups, or computers. SIDs act like security clearances for security principles within the network. Objects can also be identified using their distinguished name or their relative distinguished name.
Assigning Object Permissions in Active Directory
You can assign permissions to objects by using Active Directory Users and Computers, a snap-in for Microsoft Management Console (MMC).
Objects can be referenced by name by using:
- Distinguished names: Analogous to absolute paths of objects within a file system. The distinguished name of an object specifies complete information about the object’s location within Active Directory and includes the domain name, names of OUs that it belongs to, and the name of the object itself. Each object in Active Directory must have a unique distinguished name.
- Relative distinguished names: Analogous to relative paths of objects in the current directory of a file system. The relative distinguished name of an object is the portion of the distinguished name that is unique to the object. Any two objects in the same OU must have unique, differing relative distinguished names.
Managing objects in Active Directory
Active Directory objects can be created, deleted, and modified using the Active Directory Users and Computers (ADUC) console. You can access the ADUC using the following method:
- Go to Start → Administrative Tools.
- Among the list of available tools, select Active Directory Users and Computers.
The ADUC console will open. To learn more about the ADUC console, you can read this article.
Creating an Active Directory Object
Once you have opened the ADUC console, you can perform the following steps to create an Active Directory object. Here’s how you can create a user object
- On the Active Directory Users and Computers console, right-click on the container within which you want to create an object.
- In the menu that pops up, click New, and then User.
- In the window that pops up, add the attributes for the user object as necessary such as the user logon name, first name and last name, and password.
- Once completed, click Finish.
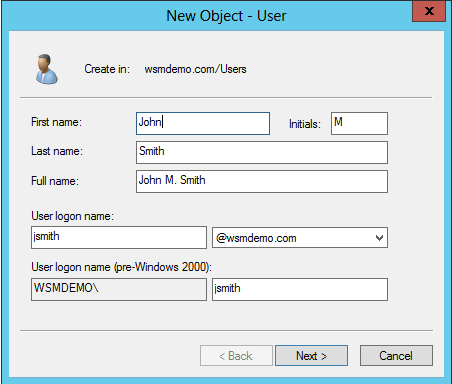
You will have created a new user object. To verify, expand the container where you chose to create the user, and you will find it.
Types of objects in Active Directory
There are two types of AD objects, which are:
- Container objects: These objects can contain other objects within them. Groups and organizational units (OUs) are examples of container objects.
- Leaf objects: Leaf objects cannot contain other objects. These objects are only representations of resources in the AD network. Users, computers, and printers are examples of leaf objects.
Various objects in Active Directory
The following are some of the common kinds of objects in an AD network:
- User: A user object represents a user account of an individual who needs access to resources in an AD network. The user account has a user name and is authenticated using a password to prevent unauthorized individuals from accessing the network’s resources. Active Directory has two types of user accounts namely:
- Administrator account: a full-fledged permanent account that has higher privileges for administrative purposes
- Guest account: a temporary account that has limited access to resources and limited permissions
- Computer: A computer object represents a workstation or a server computer in the AD network.
- Contact: A contact object contains contact information of people who are associated with but not a part of the organization. For example, vendors, service technicians, etc.
- Group: A group object is a container object that contains users, computers, and other groups. Groups are used to manage AD permissions where all the objects within a group will inherit the permissions assigned to the group.
- Organizational Unit (OU): An organizational unit is also a container object that can contain users, computers, groups, or shared folders. OUs are used for organizational purposes, manage resources within an organization, and delegate control among objects within the OU.
- Printer: A printer object represents a printer resource in an AD network
- Shared folder: A shared folder object is a pointer for a specific shared folder that points towards where the folder in question is located. The pointer does not contain any data from the folder.
Difference between groups and organizational units
It can be quite confusing to distinguish between groups and OUs as both are container objects on the surface level. However, there are key differences in the purposes of these two objects.
Groups are used to assign and control permissions to objects within the groups. Groups can also be added to access control lists (ACL) which define the permissions for the objects that are added to it.
Organizational units, as the name suggests, are used to organize AD objects. This organization using OUs is used for activities such as deploying configuration changes or delegating roles. OUs are handy when an administrator wants to delegate administrative roles to a few objects but not give complete administrative access.
One thing to note is that OUs can contain groups and other OUs. However, while groups can contain other groups as sub-groups, they cannot contain OUs within them
Another key difference is that groups have security identifiers (SID) while OUs don’t have SIDs. A SID is a unique identification value assigned to security principles (users, computers, and groups). Security principals are objects that can be authenticated by a system. Think of SIDs as security clearance for the objects within the AD network. You can learn more about SIDs over here.


