Have you ever been frustrated why your account is getting locked out frequently in active directory? If your AD account keeps getting locked out, then you have come to the right place.
Account lockouts are the biggest problem experienced by Active Directory (AD) users. They also account for the highest number of calls to IT support. Apart from users forgetting their login credentials, using a system that hasn’t been updated with new credentials is the major reason for AD account lockout. Let’s take a look at some of the reasons that an AD account might be locked out.
Reasons for AD account lockout
1. Credentials haven’t been updated
A user might have logged in to one account via multiple devices, but a password has only been changed on one device. In this scenario, the credentials need to be manually updated on every device that the account is logged in to. Failure to do so results in the AD account being locked out.
2. Cached credentials or old credentials
If a user is logged on to multiple devices simultaneously, the cache in some of the devices may still be using the old credentials to verify and grant access. This can also result in account lockouts.
3. Windows services using cached credentials
Windows services are sometimes configured to use specific AD user accounts. If the credentials are not updated after a password change, Windows services will continue using the old credentials, leading to an AD account lockout.
4. Scheduled tasks with old credentials
If there are any tasks in an AD account that were scheduled before the credentials were been changed, the account might get locked out. The scheduled task will try to proceed with old credentials unless new credentials have been updated.
5. Setting a higher bad password threshold
Typing in the wrong credentials mistakenly is another leading cause of AD account lockouts. A minimum of 10 tries before the account gets locked is a must as the possibility of a brute-force attacker getting the password right within 10 tries is not very likely.
How to resolve an AD account lockout using a Microsoft tool:
Microsoft has a tool called Microsoft Account Lockout that helps diagnose or resolve account lockouts since they’re so common. Follow the below steps to resolve an AD account lockout:
- Install the tool.
- Go to the instillation directory and run the LockoutStatus.exe file.
- Go to File and select a target for more information on the locked out account.
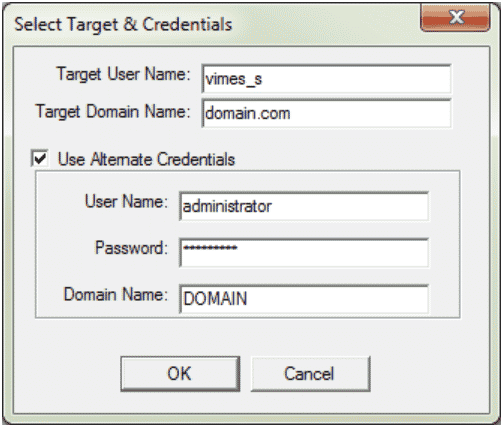
- Of the data presented to you, the domain controller (DC) with the highest number of failed login attempts is most likely the one that authenticated your user.
- In the security log of the DC, a corresponding code for the error that triggered the account lockout will be shown.
- From these steps and through the DC, you can identify the client and its ID number.
- Identify and visit the DC and the respective client server where the failed login attempt occurred, then take the necessary actions to rectify and unlock the account.
How to prevent frequent AD lockouts:
- Monitor applications, Windows services, processes, and devices for expired credentials.
- In the event of multiple account lockouts, all the event logs of a device need to be processed to identify if a cyberattack is underway. The event ID for invalid credentials is 4740. The Kerberos event ID for an incorrect password entry is 24, and 23 for trying to log in using an expired password.
- Ensure that both the DCs as well as the client-side servers have the latest updates.
If you are interested in knowing how to edit AD Account Lockout Policies, check out the embedded link.
While Microsoft Account Lockout is the most widely used tool for AD account lockouts, it does have a few drawbacks, the main one being that it can only find the reason behind account lockouts if the system is running on Windows Server 2003 or below. Microsoft Account Lockout traces which applications are sending incorrect passwords, but it cannot be used in a number of instances because it may prevent the Exchange store from starting. With ManageEngine AD AuditPlus, you can detect AD account lockouts faster with real-time alerts and troubleshoot lockouts effectively by tracking down the source of authentication failure.