Administrator accounts are the most critical and powerful accounts in operating systems, devices, and Active Directory. Administrator accounts have complete access to all the files, domains, and services on a local server. They are used to create or delete users, designate user rights, and control permissions on a server.
An administrator account is the number one target for any hacker trying to breach a network. Therefore, it is vital to carry out stringent security measures to protect administrator accounts from perpetrators. Here are some of the ways with which we can secure an administrator account in Active Directory.
1. Creating duplicate administrators and building strong passwords
Cyberattackers usually look for an administrator account, as it gives them complete access over Active Directory. Therefore, creating duplicate users with similar administrator-level access along with renaming the original admin accounts and disabling them makes identifying administrator accounts a difficult task for threat actors. Additionally, strong passwords can help prevent unauthorized access to accounts and make them harder for threat actors to crack. The password should contain an array of uppercase and lowercase letters with a combination of numbers and special characters.
2. Disabling local administrator accounts
Every domain environment has local administrator accounts, which are enabled by default. If the attackers manage to compromise and control one local administrator, it can give them rights to all the devices under this local domain. Accessing multiple local administrator accounts in different domains can give way to severe security threats in an Active Directory environment. Therefore, it is crucial to perform admin tasks with the individual account and not the local admin account.
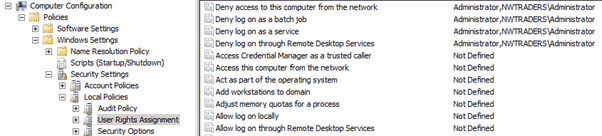
You can use these policies to configure GPOs to restrict the local administrator account’s use on domain-joined systems:
- Deny access to this computer from the network.
- Deny log on as a batch job.
- Deny log on as a service.
- Deny log on through Remote Desktop Services
3. Implementing secure admin workstations (SAMs)
SAMs are workstations created specifically for accounts to perform administrative functions in Active Directories, domain controllers, and servers. Separating sensitive tasks and accounts from typical workstations provides robust protection from phishing and credential-stealing attacks. SAMs should:
- Never rely on a single factor of authentication when an administrative account executes any privileged activity. Multi-factor authentication should be enabled for every action that is taking place in the workstation.
- Implement physical security standards such as key logging and tracking data transfers via USBs to keep unauthorized activities in check.
- Use drive encryption to ensure that the data on the drive is inaccessible in case of theft.
4. Removing members from the local domain admin group
Members of a domain admin group have excessive privileges, such as rights to install or uninstall programs, reset passwords, disable users, etc. These privileges can be exploited by attackers when they infiltrate a network. Here are the steps you can take to remove users from the domain admin group using Group Policy.
Select Create a GPO in this domain, and Link it here.
Step 1: Right-click on the organizational unit where the GPO is to be applied.
Step 2: Name the GPO and select OK.
Step 3: Right-click the GPO and choose Edit.
Step 4: Navigate to Computer Configuration > Preferences > Control Panel Settings > Local Users and Groups.
Right-click on Local Users and Groups and select New > Local group.
Choose Local Group from the list.
For the Action, choose Update.
For the Group Name field, select Administrators (built-in).
Check the boxes next to Delete all member usersand Delete all member groups.
In the Members section, add all the members to be deleted.
Click Apply to delete the users and groups that you want to remove from the local administrator group.
5. Monitoring Active Directory events using third–party applications
Performing Active Directory monitoring with a SIEM solution can help detect anomalous behavior in the network. Logs can help us see patterns and analyze if security compliance is kept intact. ManageEngine Log 360 is a SIEM solution with prebuilt Active Directory security reports. Implementing this solution can help you monitor changes in your Active Directory environment and take the necessary steps if a security breach is detected.