What you will learn:
Active Directory has a strong authentication mechanism such as the Kerberos authentication mechanism, that prevents malicious intruders from gaining access to resources within the network. However, this mechanism is not sufficient to ensure the safety of information. For example, an attacker could compromise a user account with a weak password, or there might also be an insider who could misuse the network’s resources. Hence, Active DIrectory has numerous policies that can be configured. These policies tackle various management and security aspects of the network. In this article, we will take a look at one set of policies called Active Directory Account Policies. We will dive into what Account Policies policies are, and how they are classified.
What are Active Directory Account Policies?
Active Directory (AD) Account Policies are a set of policies that are associated with the authentication mechanism of user and computer accounts. Until Windows Server 2008, there could only be one Account Policy for a domain, and all users and computers within that domain should adhere to the Account Policy configured to the domain. One exception is if there is any Account Policy associated with an OU within the domain. In such cases, the user and computer objects within the OU will adhere to the AD Account Policies associated with their parent OU.
Classification of AD Account Policies:
Account Policies are classified into two categories. They are as follows:
- Password policies
- Account Lockout Policies
What are Password Policies?
Password Policies are a set of policies that determine how a password should be set for an AD user account. Depending on the configuration, the Password Policies can either set to be stringent or lenient, but it’s better to have stronger password policies to ensure that it is not easy for an attacker to guess the passwords.
There are six different password policies in AD. They are as follows:
- Enforce Password History : This setting determines the number of new passwords that have to be set, before an old password can be reused. It ensures that old passwords are not used continuously by users which will render the Minimum Password Age policy setting useless.
- Maximum Password Age : This setting determines the maximum number of days a password can be used. Once the Maximum password age expires, users must change their password. It ensures that users don’t stick with one password forever.
- Minimum Password Age : This setting determines the minimum number of days a password must be in use before it can be changed. Only when the minimum password age expires, users are allowed to change their password. It ensures that users don’t change their password too often.
- Minimum Password Length : This setting determines the minimum number of characters a password should contain.
- Passwords must meet complexity requirements: This setting determines whether the password must meet the complexity requirements specified. The various available complexity requirements are:
- Not contain the user’s account name or part of the user’s full name that exceed two consecutive characters
- The password is at least six characters long
- The password contains characters from at least three of the following four categories:
- English uppercase characters (A – Z)
- English lowercase characters (a – z)
- Base 10 digits (0 – 9)
- Non-alphanumeric (For example: $, #, or %)
- Store Passwords using reversible encryption: This security setting determines whether the password is stored using reversible encryption. If a password is stored using reversible encryption, then it becomes easier to decrypt the password.
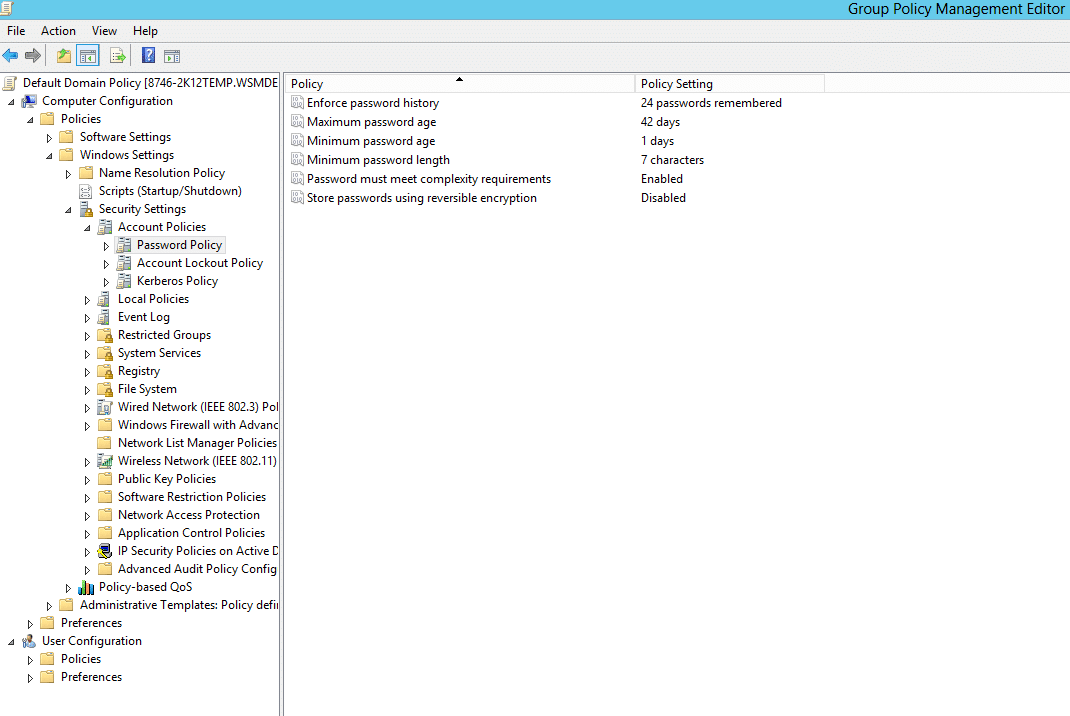
You can learn more about AD password policies in this article.
What are Account Lockout Policies?
Account lockout policies are a set of policies that define the instructions for how the account should be handled in case of a failed logon attempt. This policy comes in handy in case of a brute-force or dictionary attack attempt. There are three Account Lockout Policy settings. They are as follows:
- Account Lockout Duration: This policy setting determines the duration for which an account would remain locked out after a defined number of failed logon attempts, before the account gets unlocked again.
- Account Lockout Threshold: This policy setting determines the number of failed logon attempts after which the user gets locked out of the account.
- Reset Account Lock-out Counter After: This lockout policy setting determines the duration after which the failed logon attempt counter is reset to 0.
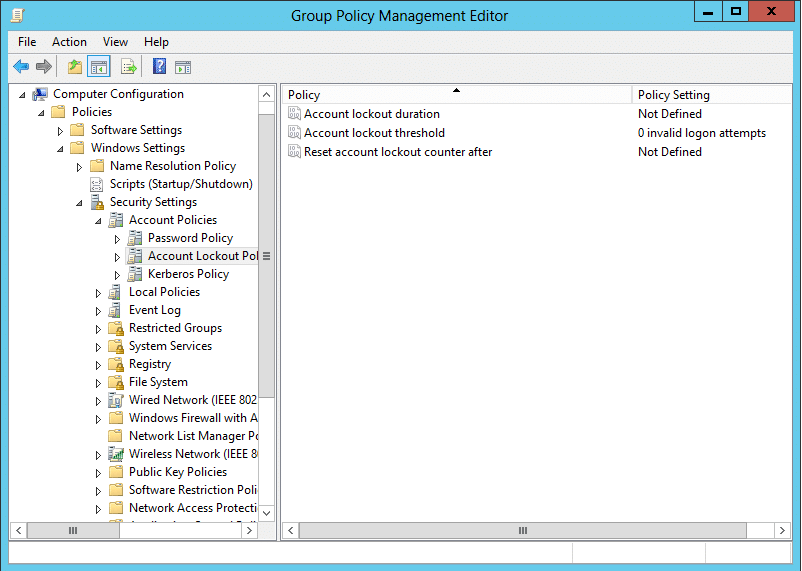
You can learn more about AD Account Lockout Policies in this article.
Fine-grained password policies:
The Account Policies are linked to domains using Group Policy Objects (GPO). You can learn more about GPOs and how they function in this article. As mentioned earlier, there can only be one Account Policy setting linked to a domain. This was the case until the introduction of Windows Server 2008. To allow administrators to enforce different policies to different sets of users, Microsoft launched a new functionality called fine-grained password policies (FGPP) in Windows Server 2008. These policies can be set in what is called password setting objects (PSO). FGPP is a derivative of account policies, so that means it includes not only password policies, but also account lockout policies. You can learn more about FGPP in this article.
People also read






